Cybercrime is a thriving high reward low-risk business model, and it can be summed up easily with just-$.
In the past, there were various obstacles to overcome in order to get into the cybercriminal game. The ‘original cybercriminals’ ran a centralized operation which  owned the servers and constructed malicious software (malware) from scratch.
owned the servers and constructed malicious software (malware) from scratch.
This business model proved to be incredibly expensive to operate and exceedingly time-consuming; in order to make a substantial profit, large organizations were the only option.
However, similar to other ecosystems, the cybercriminal ecosystem continues to evolve.  Today, it is a distributed system where anyone with an agenda can simply rent, lease or purchase an ‘as a Service,’ services and ‘cash in’ on their crimes.
Today, it is a distributed system where anyone with an agenda can simply rent, lease or purchase an ‘as a Service,’ services and ‘cash in’ on their crimes.
Some of the more of the well-known as a Service, services include:
- Malware as a Service (MaaS)
- Distributed Denial of Service as a Service (DDoSaaS)
- Ransomware as a Service (RaaS)
- Hacking as a Service (HaaS)
- Money Laundering as a Service (MLaaS) to name a few.
The distributed system requires less effort because the criminals take advantage of the current ‘trends’ including the ‘human factor,’ where one in three individuals within an organization, regardless of training, will click on a phisher’s email and/or ‘low-hanging fruit’ otherwise known as the persons or organizations that despite all the warnings incur the risks with sub-par security, found easily by an exploit kit. Rather than deploying sophisticated and expensive Zero-Day attacks, now, any endpoint becomes a potential source of revenue.
As a Service, services is a flourishing business model run on the black markets found on the DarkNet such as the TOR network. TOR is a technological revolution in the  facilitation of cybercrimes, because of the anonymity under which groups are able to operate.
facilitation of cybercrimes, because of the anonymity under which groups are able to operate.
Cybercriminals commit crimes directly against individuals, organizations, or governments through means such as malware attacks.
Direct methods are when resources are taken directly from the victim including
- Emptying bank accounts
- Stolen Financial Information
- Stolen Access Credentials
- Phishing
- Malware, i.e., Viruses, Worms, Trojans, and RATs
The criminals also attack in indirect manners including identity theft and fraud.
Indirect methods involves information obtained covertly from the victim which can be sold on the DarkNet including
The introduction of the cloud computing as a Service, services paradigm has brought abundant  advantages to the information technology industry but also greater opportunities for cybercriminals.
advantages to the information technology industry but also greater opportunities for cybercriminals.
Cybercriminals no longer need to rely on their own skills and assets to carry out exploits.
Several of these services include
- Infrastructure as a Service (IaaS) provides the rental of servers and storage devices.
- Software as a service (SaaS) provides the infrastructure enabling the dynamic production of applications.
- Data as a Service(DaaS) Data is stored in the cloud and is accessible by a range of systems, and devices.
- Platform as a Service( PaaS) allows users to develop, run and manage applications without the complexity of building and maintaining expensive infrastructure and the space required to develop and launch applications.
These cloud-based technologies afford cybercriminals with greater flexibility, greater resource management and agility in the furiously-paced technological environment allowing for even-more-dangerous and aggressive exploits.
Cybercriminals have taken full advantage of these services because they eliminate the need to maintain their own infrastructure, they can facilitate better operational security (OpSec) which adds a layer of obfuscation between the cybercriminals and the organizations hunting them while efficiently creating and distributing their malware attacks.
Another fuel for as a Service is the rise and popularity of cryptocurrencies. Cryptocurrency is digital money that utilizes a decentralized, peer-to-peer (P2P) payment network thus making it harder to discover criminal activity.
digital money that utilizes a decentralized, peer-to-peer (P2P) payment network thus making it harder to discover criminal activity.
The most utilized form of cryptocurrency is Bitcoin.
Bitcoin is used globally for legitimate organizations but is better know for the criminal exploits.
The topic of Bitcoin would not be complete without addressing the processes of Tumbling. Tumbling essentially adds an additional layer of anonymity to block attempts to track and uncover Bitcoin transactions. There are multiple ways to Tumble Bitcoins including
- Multiple Wallets Cybercriminals creates a wallet via TOR and adds Bitcoins to it. A
 second wallet is created, again, utilizing TOR, and moves the funds into the second wallet. Last but not least, a third wallet is created, and the funds are moved again, thus confusing the trail of transactions between the three wallets making attribution almost impossible.
second wallet is created, again, utilizing TOR, and moves the funds into the second wallet. Last but not least, a third wallet is created, and the funds are moved again, thus confusing the trail of transactions between the three wallets making attribution almost impossible.
- Third Party Services DarkNet organizations offer services in order to launder
 bitcoins which add a ‘proprietary obfuscation technology’ that breaks the link to the source of the funds and prevents any blockchain analysis tracking bitcoin transactions.
bitcoins which add a ‘proprietary obfuscation technology’ that breaks the link to the source of the funds and prevents any blockchain analysis tracking bitcoin transactions.
The DarkNet is an encrypted network built on top of the DarkWeb. Two typical DarkNet  types are P2P used for file sharing and networks such as TOR for anonymity.
types are P2P used for file sharing and networks such as TOR for anonymity.
 TOR which is short for ‘The Onion Router,’ provides anonymity to its users by bouncing the user’s communications around a distributed network of relays worldwide; TOR also prevents tracking of what sites are visited, prevents the sites visited, from learning the user’s physical location, and allows access to .onion sites ranging from legal to absolutely illegal. TOR can be used on Windows, Mac OS X, or Linux without any additional software.
TOR which is short for ‘The Onion Router,’ provides anonymity to its users by bouncing the user’s communications around a distributed network of relays worldwide; TOR also prevents tracking of what sites are visited, prevents the sites visited, from learning the user’s physical location, and allows access to .onion sites ranging from legal to absolutely illegal. TOR can be used on Windows, Mac OS X, or Linux without any additional software.
As with all things as a Service, where there is a need, service providers seem willing to satisfy it. Moreover, as long as the return on investment (ROI) remains high, the expectation for continued investment into even more resources in order to unleash greater numbers of cybercrimes on the broadest possible range of targets will continue. Buckle up your seatbelt.
Prevention Guidelines
- Use strong passwords- Eight characters. Include upper and lower case letters, Numbers and Special Characters (!@#$%^&*(
- Adding just one capital letter, and one special character changes the Brute Force processing time for an 8 character password from 2.4 days to 2.10 centuries. Think about that!

- Adding just one capital letter, and one special character changes the Brute Force processing time for an 8 character password from 2.4 days to 2.10 centuries. Think about that!
- Never write your password on a sticky for an intruder to find.
- Group the sites you visit into categories, i.e. business, personal, sensitive, and use a password for each category.
- Activate your Firewall- it is the first line of defense.
- Use your Anti’s
- Anti-Virus
- Anti-Malware
- Anti-Spyware
- Secure your Mobile Devices-They are just as vulnerable as your computer.
- Install the latest OS updates.
- Download Applications and Attachments FROM TRUSTED SOURCES ONLY.
- Delete all unknown e-mails.
- Use encryption for all your sensitive data.
- Use HTTPS for all your transactions.
- Backup your data frequently and store it in multiple locations.
Cybersecurity is a shared responsibility. Stop. Think. Connect.


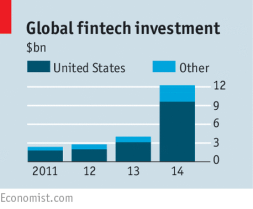 most profitable elements-mobile payments to insurance. Industry analysts estimate that traditional financial services industries could be at risk of being lost to standalone FinTech companies within 5 years.Additionally, FinTech is making an impact on the industry tripling to more than $9+ billion in the US in 2014 alone. (Economist.com)
most profitable elements-mobile payments to insurance. Industry analysts estimate that traditional financial services industries could be at risk of being lost to standalone FinTech companies within 5 years.Additionally, FinTech is making an impact on the industry tripling to more than $9+ billion in the US in 2014 alone. (Economist.com)